Risk Intelligence: Detect and Mitigate Risks
What is Competitive Intelligence, really? As many Competitive Intelligence professionals will probably tell you, it depends mostly on your organization’s objectives. In this multi-blog series, we explore types and uses of competitive intelligence. We will draw on client experiences, who are leaders in industries ranging from security, banking, and manufacturing.
Risk monitoring or risk intelligence, although it varies by industry, can be defined as the anticipation and detection of all possible risks that could affect your organisation and the creation of contingency plans, response protocols and communication strategies.
Why it's essential to implement a rigorous risk intelligence strategy:
- Gain accurate knowledge of your environment and understand where you are vulnerable.
- Clearly represent or define your risks (this process can also be called "risk mapping", and usually involves mapping your risks on a graph, map or other visual representation, and is an essential risk management tool).
- Monitor your risks (or factors that could become risks) closely.
- Take strategic action to avoid risks by finding ways to prevent them or by improving your response time and efficiency when a risk becomes a reality.
But what risks should you be looking out for? The following non-exhaustive list will give you an initial idea:
- Economic
- Social
- Geopolitical
- Legal and normative
- Country
- Ecological
- Technological
- Security
- Employee / staff (prevention of data leakage)
- Reputation
1. Plan, Plan, Plan
Although risk intelligence can be used for many purposes, it is important for organisations to put a rigorous methodology in place to control or at least detect and anticipate risks.
- Brainstorm all possible risks that could affect you, your organisation, your partnerships, your sector, your country, etc. Involve as many people as possible from other business units, as they have excellent knowledge of your environment. When you first identify potential risks, do not exclude anything.
- Once you have identified all the possible risks, determine how these risks could affect you. Risk typologies should be associated with each risk.
- Evaluate all types of risk according to the likelihood of occurrence and severity
- Write down the different types of scenarios related to the identified risks, grading them according to ease of implementation, and assumptions of favourable and unfavourable reactions.
- Create plans to mitigate these risks and plans to respond to these risks in the event that you are unable to stop them effectively.
- Now define your monitoring parameters to monitor these risks.
)-2.png?width=557&height=341&name=Severity%20(Instagram%20Post%20(Square))-2.png)
Risk assessment and prioritisation of risks
2. Choose Broad, But Specific Topics
When you are monitoring for the purposes of risk intelligence, your monitoring/search parameters will be both considerably broader and incredibly specific. Competitive intelligence for risk is different from other applications of competitive intelligence.
If you are monitoring for the purpose of risk management, you would need to watch for:
- Industry news
- New regulations/changes in laws
- Supplier news
- Risks in the countries you operate in
- Security threats
- Safety threats
- Innovations
- Political changes
- Scandals/ethical issues
- Natural risk/disasters
- Economic risks
- Competitors
- Industry changes
- Cyber threats*
* Note that it is extremely difficult to anticipate a cyber attack on you, but you can try to protect yourself by listing the most recent types of viruses or cyber attacks and setting up a response plan, organising simulations and stress tests.
This list may seem scary at first: how can you monitor all this information? What if you are a global manufacturing company with factories and suppliers all over the world? How do you monitor all these issues in all the countries you operate in?
3. Be Organized And Use Technology, Because You Can’t Do It Alone
As mentioned earlier, risk mapping is a way of visually representing risks in terms of likelihood of occurrence.
When conducting a risk intelligence project, it is highly recommended that you use data visualization tools to help keep track of all of your information. If you can link your monitoring tool to data visualization tools, you can establish a virtual risk management map, or a sort of risk management “war room” to see when a section of the globe you monitor is receiving a lot of attention from social media or the news. Imagine if you had all of your information automatically imported into a data visualization map. If you see that the city that your factory is located in is suddenly lighting up, you could check the associated mentions to identify what risk is occurring, and immediately deploy your risk mitigation plans.
4. Deliver Information Rapidly
It is highly recommended that you set aside a significant amount of time before setting up your project to list all possible risks and determine responses to all of these events.
Senior management and key stakeholders should be heavily involved in this process, as well as several key departments (for example, your public relations department should establish response scenarios to an industrial accident, a breach of a new regulation or a reputational issue in advance).
For deliverables, immediate news alerts are probably the most effective. If you see a theoretical risk is about to become a real risk, you won't have time to wait a week and create a newsletter. Employees, management, and key stakeholders will need to know about it immediately . Set up alerts for every hour or for special keywords, and ensure key players receive these alerts so they can act quickly.
5. Risk Intelligence in Action
Take the example of an entertainment company located in the outskirts of a city with millions of visitors per year.
Now let's look at the risks that the company would monitor:
- Public transport strikes: these represent a very important risk as they paralyse part of the traffic and can discourage potential customers from travelling.
- Changes in the price of potatoes: this may seem surprising, but part of the leisure park's turnover is based on the catering it provides for its visitors. If the stock market price has an adverse effect on the price of the main food items, then sales will plummet, which will have financial consequences for the park.
- Economic news from the region: let's imagine that an indirect competitor (e.g. a wellness & aquatic centre) sets up in the vicinity of the park. The park must then assess the impact of this change in order to decide on the nature of the risk, the potential repercussions and the strategy to adopt: should the park lower its prices, offer new services to counter this new competitor, or propose a partnership to limit the effects on its activity? This is the kind of question that risk intelligence must answer.
- Employer risk: given the nature of its activity, the company is more sensitive than others to work-related accidents. It must therefore keep a rigorous watch on labour law to ensure that it does everything in its power to prevent these accidents.
6. Reaching Further: The Invisible Web
Should you monitor the invisible web as part of your risk intelligence strategy? Is it worth it? Before answering this question, let's look at the definition of the invisible web. Did you know that the invisible web represents 96% of the entire web, while the publicly accessible web represents only 4% of the content? Imagine the amount of information available! The deep web is all the content that is not indexed by search engines (e.g. Google, Bing). It is very difficult to access without knowing the precise address. The deep web holds a certain amount of information:
- User databases
- Corporate intranets
- Websites protected by an authentication processes
- Academic information
- Medical records
- Banking data
- Sites using exclusively misunderstood technologies of indexing robots
"Deep Web" simply refers to areas of the Internet that are not indexed by search engines like Google and Bing. It is very difficult to access it without knowing the exact URL. The deep web hosts a certain amount of information including:
In contrast, the Dark Web refers to a subcomponent of the Deep Web. Accessing it requires the use of specific encrypted browsers — such as Tor or I2P — that conceal the identity and location of the user. Different sites that can be found include drug trafficking, firearms, organs transfer, private communications, child pornography, purchase of malware, etc.
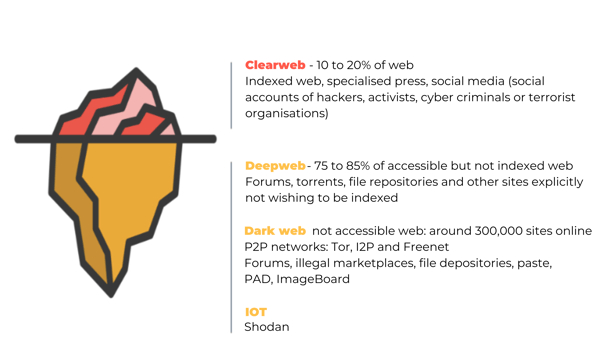
Not all risk intelligence professionals will find it useful to monitor the invisible web. This realm brings interesting perspectives for organizations wishing to monitor the following topics:
- Illegal trade
- Personal / banking / health data traffic
- Cyber security
- Political demands, activists
- Whistleblowers
- Terrorist networks
A recent example occurred prior to the implementation of Europay MasterCard Visa (EMV) in the U.S., when intelligence from the Deep & Dark Web enabled a team of analysts to uncover a plot to exploit the EMV rollout. While monitoring certain underground communities, analysts discovered a group of threat actors had developed an EMV-chip recording software, as well as manufacturing techniques needed to fabricate chip-enabled credit cards that were allegedly capable of bypassing even the most robust anti-fraud controls. Upon being made aware of these findings, financial services institutions were able to adjust their EMV implementation strategy and security measures to prevent the threat becoming reality.
Source: IT Security Guru
In Summary
The more an organization adopts an anticipatory posture, by combining a precise and perfectly up-to-date knowledge base of its environment and its vulnerabilities, the more it will be able to protect itself against risks and build appropriate response protocols.
How to Do Competitor Benchmarking on Social Media?
Written by Malena Dolff Gonzalez
Malena is a digital marketing intern specialising in the NE and DE regions at the Paris Digimind office. She is half German and half Spanish and is currently pursuing a Bachelor with a focus on business and social psychology at University College London. Outside of the Digimind offices she enjoys cooking and traveling.


